I noticed the following tweet pass by on Twitter:
Just received my 1st-ever digitally signed piece of spam. The ribbon is bound to entice someone 2 click on the email pic.twitter.com/470TpdaPDE— Robert (Роберт) (@RobertIdAu) November 9, 2015The mail received is as follows:
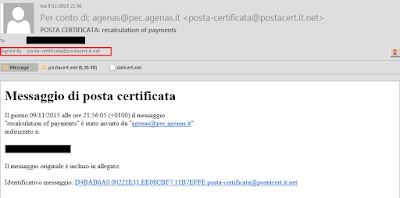 |
| Spam but digitally signed |
As Robert correctly notes, since the mail is digitally signed, it may entice people more to open the attachment and get infected. In case you're wondering, the key id of the certificate is as follows:
FE:22:B7:24:E3:4F:27:D9:05:E0:CC:B8:BD:DE:F4:8D:23:FD:2F:D9 (copy of cert on Pastebin)
Issuer: C=IT, O=DigitPA, OU=Ufficio interoperabilita' e cooperazione, CN=DigitPA CA1
 |
| Signature details. S/MIME message format |
Both first and second mail are coming from: 175.156.221.127 - IPvoid - Whois (DomainTools)
 | |||
| IP location: Singapore (VirusTotal) |
On to the attachment (the .xml file is harmless):
 |
| "recalculation.zip" attached |
Hello
This recalculation of payments for the last month.
I remind you of your debt 3148,48 AUD.
Please pay as soon as possible.
The ZIP file contains 2 files: recalculation_77979.pdf.js & info_9455.txt. The TXT file just contains the name of the first file, which tries to hide as a PDF file but is in fact JavaScript (JS).
 |
| Part of the JavaScript |
You can find the original JavaScript on Pastebin. You can also find the decoded base64 here and the final obtained JavaScript here. In the final JavaScript, you'll see it downloads a file and renames it to a random filename, then executes it:
| Download |
 |
| Run |
It fetches a file from: 203.255.186.156 - IPvoid - Whois (DomainTools)
 |
| IP location: Korea (VirusTotal) |
The eventual payload may be Andromeda/Gamarue, which will make your machine part of a botnet. Some information on the dropped DLL file (this is all static analysis):
Meta-data
==================================================================
File: 28236726.dll
Size: 495630 bytes
Type: PE32 executable for MS Windows (DLL) (GUI) Intel 80386 32-bit
MD5: 934df5b173790da14ef3a817ec1fc422
SHA1: e90b6e45f255350d0fd4cba361a09ad5d8271af1
ssdeep: 12288:GysxmAb/DC7BfWLc9ivHsegWDhNSKDWrV5rJfT:jo768wAAExDoPr9
Date: 0x429CE7C3 [Tue May 31 22:40:03 2005 UTC]
EP: 0x1000bddb .text 0/5
CRC: Claimed: 0x0, Actual: 0x83498 [SUSPICIOUS]
Packers: Armadillo v1.xx - v2.xx
 |
| Functions in our DLL file |
You may also find the file on VirusTotal, SHA1 hash: e90b6e45f255350d0fd4cba361a09ad5d8271af1
There's also an analysis available by Reverse.it (Hybrid Analysis) on Windows 7 32bit & Windows 7 64bit. Feel free to perform any additional research on it, let me know if you find something interesting or should you find out exactly which kind of malware this is.
Just as a note, while all that is happening in the background, a decoy PDF file gets opened as well, as to not raise suspicion:
 |
| Decoy PDF document (not malicious) |
Prevention
For administrators:
- Sender's end: Create an SPF record, as to prevent sender address forgery. More on SPF here.
- Receiver's end: Turn on SPF checking on your mailserver.
- If possible, turn on full support for DMARC. More on DMARC here.
- Check that only your mailserver may access the WAN (or RED) on port 25. Configure this in your firewall.
- Check that you use strong passwords for your Domain Controller server(s).
- Check that antivirus is installed, up-to-date and running on all workstations. (if applicable)
- If not needed, you can disable Windows Script Host (WSH), as it's needed for JavaScript to run locally. Read how to do that here.
For endusers:
- Don't open attachments from unknown senders - ever.
- Install an antivirus and keep it up-to-date and running. Enable the option to scan Compressed Files.
- Preferably, see that your antivirus has a firewall as well, to prevent unauthorised access.
- Consider disabling Windows Script Host. You can use my tool, Rem-VBSworm with option D for example.
- Alternatively, you can install Analog X's Script Defender, which will block these scripts (JS, VBS, ...) as well.
Disinfection
As usual:
- Look for suspicious Run keys (find locations here) and delete the associated file(s).
In our case, all files were dropped in the %TEMP% folder. Also, don't forget to look for rundll32.exe processes, as the payload was a DLL file. More information on rundll32 here. - Run a full scan with your installed antivirus product.
- Run a full scan with another antivirus and/or antimalware product.
- In a company: warn your network administrator immediately!
Conclusion
Now how was that mail sent out? There's no sure way of telling - it's possible the company is compromised (by either malware or an attacker), there's no SPF record, the certificate has been stolen (unlikely but not impossible), .... Most likely, a machine is infected by a spambot.
Note that with PEC (Posta Elettronica Certificata), a user can send a signed message even when the mailserver is not compromised. PEC means the server signs a message to ensure timestamp and sender, not content. More on PEC here (ITA) or here (EN). See also point 2 and 4 in the Prevention tips above.
I've contacted all related parties and hoping I'll get a reply soon, or at the very least they will perform some analysis and cleaning.
Follow the prevention tips above to stay safe. If you're looking for Indicators of Compromise (IOCs), they can be found as usual on AlienVault's OTX.