It's the exploit season (especially for Java).
This time, I'm seeing a lot of mails supposedly from PayPal:
 |
| Apparently you bought an expensive watch. For someone you don't know. Looks legit. |
Originating IP of this mail:
188.33.40.190 - IPvoid Result
Seems to be sent out by the Cutwail botnet.
 |
| Adobe Reader giving a warning |
Firstly, a blank webpage opens up and you're getting a PDF or Java exploit which is being launched.
Adobe crashes with a warning. Should raise some suspicions.
The latest trick the malware authors perform is to ultimately redirect you to a fake pharmacy:
 |
| 'Pharmacy Express'. Fake pharmacy. |
You are eventually ending up on this page, probably to make you think 'it was just Viagra spam, that's all'. Wrong! In fact, you're being infected as we speak. A file gets dropped to the %appdata% folder:
xydyswylmylh.exe
Result: 6/45
MD5: 22f3c0fd2a5d9e1799699097836bb5dc
VirusTotal Result
ThreatExpert Result
Anubis Result
There were a lot of HTTP connections, possible password stealer?
Pastebin link: http://pastebin.com/6LhCfu6q
Additionally, it connects to the following IPs & ports:
Pastebin link: http://pastebin.com/LDrzfKHN
Malware was downloaded from:
188.93.211.151 - IPvoid Result
Adobe/PDF exploit being used: CVE-2010-0188 - CVE Report
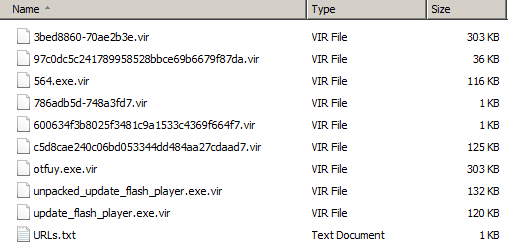
All files gathered, contact me for a copy:
 |
| Gathered files in this attack |
This spreading is still going on, if you'd like to know the source of these exploits (be careful though, they can still be live!), you can see these results from URLquery:
- Don't click on any link(s) of unknown senders.
In fact, don't even open mail from unknown senders. - Have you paid for an expensive watch for somebody you don't even know? I didn't think so.
- Install an antivirus and antimalware product and keep it up-to-date & running.
- Use for example NoScript in Firefox to counter these attacks.
- And above all: patch Java, Adobe and any other 3d party software you may have!