Is this the perfect recipe for a cybercriminal ?:
- Hacking LinkedIn's password (and possibly user-) database.
- Sending an email to all obtained email addresses, which is urging you to check your LinkedIn inbox as soon as possible.
- A user unawarely clicking on the link.
- An exploit gets loaded. Malware gets dropped. Malware gets executed.
- User's computer is now a zombie (part of a botnet).
I would definitely say
YES.
A reader of my blog contacted me today, he had received an email from LinkedIn which was looking phishy. We can verify that Step 1 is accomplished, by the simple fact that in the "
To" and/or "
CC" field of the email below, there are about ~100 email addresses. A quick look-up of a few of them on LinkedIn reveals the unconvenient truth...
Here's the email in question:
 Reminder from LinkedIn. You got a new message !
Reminder from LinkedIn. You got a new message !Subjects of this email might be:
"
Relationship LinkedIn Mail", "
Communication LinkedIn Mail", "
Link LinkedIn Mail" or "
Urgent LinkedIn Mail". No doubt the subjects of this email will vary, and are not limited to these four.
Step 1 and step 2 of the cybercrook's scheme are already fulfilled. Now he just has to wait until someone clicks on one of the links. Which brings us to point 3.
Suppose someone clicks on the link. What will happen exactly ? This depends on the version of these programs that may be installed on your computer:
In some cases, your browser will crash. In other cases, the page will just appear to sit there and nothing happens. In unfortunate cases, the exploit will begin doing its work. As said before, a mixed flavor of Adobe & Java exploits are used.
In this case, we will review the specific Adobe exploit. We will check with Process Explorer what exactly is happening:
 The green highlighting indicates the spawning of a new process
The green highlighting indicates the spawning of a new processWhat's this ? There's a process from Adobe Reader loaded under our Internet Explorer ? Which seems to spawn a .dll file ? Which in turn spawns another file .... Okay, you get the point here.
The PDF file has several embedded files, which are dropping malicious executables and executing them. After the process of spawning and dropping processes and executables, the malware will also clean-up any leftovers, including the PDF file at first:
 Message from Adobe Reader it has crashed. Have a guess why
Message from Adobe Reader it has crashed. Have a guess whyAfter the user clicks OK, everything looks fine. Right ? No, of course not. Ultimately, there's a malicious executable which will start every time the computer boots.
Interesting to note is, that there is also an attempt to exploit
CVE-2006-0003. An exploit from 2006 nonetheless !
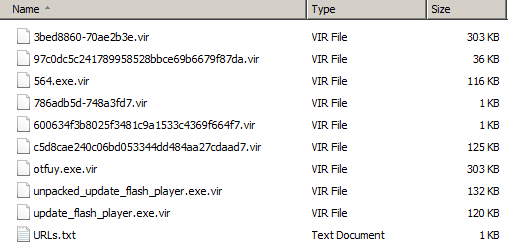
Step 3 and 4 have also been accomplished now. The user clicked on the link, the exploit(s) got loaded and the user is now infected. With what you may ask ? Well, let's review all the associated files:
The initial Java exploit -
set.jar -
(when I first uploaded this sample a few hours before this blogpost, there were ZERO detections)Result:
2/42MD5: b0697a5808e77b0e8fd9f85656bd7a80
VirusTotal Report
ThreatExpert Report
I just now re-uploaded
set.jar (
17:47:41 UTC), it has now
6 detections. Most probably the Blackhole exploit kit is responsible for this attack. Microsoft identifies the file as
"
Exploit:Java/CVE-2010-0840.NQ".
The corresponding CVE can be found
here.
"
I got Java patched, always", you might say. Great ! How about Adobe Reader ?
c283e[1].pdfResult:
11/38MD5: ad5c7e3e018e6aa995f0ec2c960280ab
VirusTotal Report
PDFXray Report
MWTracker Report
Thanks to
PDFiD, we are able to see there's an AcroForm action and 6 embedded files. Basically, AcroForm is just another way to execute JavaScript in a PDF document. Embedded files are... files hidden in your PDF document:
 PDFiD results
PDFiD resultsHere's our first dropped file -
calc[1].exeResult:
5/38MD5: 4eead3bbf4b07bd362c74f2f3ea72dc4
VirusTotal Report
ThreatExpert Report
Anubis Report
Calc[1].exe will drop other files. Examples:
amutwa.exeResult:
9/42MD5: e7e25999ef52e5886979f700ed022e3d
VirusTotal Report
ThreatExpert Report
Anubis Report
nyyst.exeResult:
10/42MD5: fbc4bb046449fd9cef8a497941457f4f
VirusTotal Report
ThreatExpert Report
Anubis Report
The malware will try to 'phone home' or connect to the following IP addresses:
188.40.248.150 -
IPVoid Result
46.105.125.7 -
IPVoid ResultThe IPs above (188.40.248.150 in particular) are part of a known botnet.
After all 4 steps have been executed, Step 5 of the process is completed as well and the machine will be successfully part of a botnet. The
Zeus botnet. For more information about Zeus, you can read upon the (limited in information, but sufficient) Wikipedia article:
Zeus (Trojan Horse)There are also numerous articles on the Zeus botnet, the takedowns by Microsoft (whether they were successful or not, I'll leave in the middle), and many other reports.
ConclusionSo, what did we learn today ? If you do not know the answer to this question, please re-read the article again.
PATCH PATCH PATCH people ! Keep
ALL of your software up-to-date ! This means Adobe, Java, but don't forget other software, for example VLC, Windows Media Player.... You get the picture.
This also includes installing your Windows patches, keeping your browser up-to-date as well as any plugins or add-ons you might have installed.
If possible, avoid using Adobe and/or Java. There are alternatives. An alternative for Adobe is for example
Sumatra PDF. Just don't forget to patch the alternatives as well !
Finally, use an up-to-date Antivirus product to keep your machine safe should you not have done any patching. Chances are you might still be infected, but are already
less likely.
If you are in a corporate or business network, take the necessary actions and include several layers of protection. This
also includes informing your users to not click on everything in an email ! Applying the appropriate Security Rights on a machine can prevent you from having a whole lot of work.... and lack of sleep ;-) .
Note:
If you are interested in the files discussed in this post, contact me on Twitter:
@bartblaze