Recently, a friend of mine encountered an interesting phishing attempt:
— Cristian Iankovszky (@cizky) January 31, 2017
The message reads:
DHL has attempted to deliver the parcel no.: 1993747, but nobody was available. Please arrange re-delivery using our mobile app: http://dhl-tracking[.]online/app.apk
In this blog post, we'll analyse the malware in question (Marcher, banking trojan) and provide disinfection and prevention advice. Click on any of the relevant links below according to your needs:
Analysis
Disinfection
Prevention
Conclusion
Resources
Analysis
When you visit the link, a file called app.apk gets downloaded with the following characteristics:
| MD5 | 80c797acf9bdbe225e877520275e15f5 |
|---|---|
| SHA1 | f255de54ffbff87067cfa7bc30d6d87a00aded8f |
| SHA256 | fcd18a2b174a9ef22cd74bb3b727a11b4c072fcef316aefbb989267d21d8bf7d |
| Package name | ijrtc.jwieuvxpjavuklczxdqecvhrjcvuho |
The application presents itself as 'DHL Express Mobile' while being installed and will ask for device administrator rights:
 |
| Figure 1 - System service |
Basically, the app can do anything it desires:
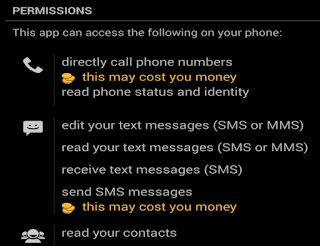 |
| Figure 2 - Permissions; this includes & reading text messages |
 | |
|
The payload, or the actual malware that is installed, is the Marcher banking trojan. Recently, it has been masquerading as applications for package delivery, such as DHL in the example above, Posta Online or an app called Alza.
Marcher checks if any of the following antivirus or security products are installed:
 | |
|
... And targets the following applications:
 | |
|
Besides targeting antivirus applications, Marcher also uses some nasty tricks to avoid removal:
- Marcher installs itself as Device Administrator, effectively making the user unable to force the process to stop or uninstall the application normally;
- When you attempt to force uninstall the application, it will show you the device administrator prompt, as seen in Figure 1, which will continue to pop-up.
All in all, the malware isn't obfuscated much, but still proves to have particular persistence mechanisms. One does not exclude the other.
If you are only here for Indicators of Compromise, please find below:
You may also want to check out my blog post which provides a plethora of options and software/tools on how to analyze Android malware:
Analysing Android files
Disinfection
Marcher proves more difficult to remove as outlined above. The best way in this case is to back up your files and reinstall your operating system.
There is an excellent article on MakeUseOf on how to get to your phone's 'safe mode', create a back-up and finally factory restore or reinstall your operating system:
Dealing with System Problems in Android: Safe Mode, Factory Reset & Restoring Backups
Alternatively, you may try the following steps to remove Marcher, which also involves going into safe mode:
- Hold down the Power button on the side of your phone until a popup appears.
- On the menu that shows up, hold down the Power Off option until a popup appears.
- Tap OK to reboot into Safe Mode.
- You should now be in Safe Mode.
- Go to Settings > Security > Device administration > Device administrators or Phone administrators.
- Tap on the malicious application.
- Tap Deactivate in the next screen. In our example:
 |
| Figure 6 - deactive the app |
- Now, go to Settings > Applications or Apps > Manage applications > tap the malicious app > Uninstall.
For normal applications that don't have device administrator rights, only the last step is sufficient.
Afterwards, change all your passwords and notify your bank to be on lookout for any fraudulent transactions. Do this also if your bank is not listed (affected banks pictured in Figure 5).
Additionally, you may want to run a scan with an antivirus or antimalware product for Android. If you're unsure which antivirus to run, you can try Avast (it also detects the Marcher version discussed in this blog post).
You may want to have a look at other antivirus products if Avast does not suit your needs. A good comparison can be found on AV-test's website: The best antivirus software for Android.
Note that the best course, in any case, is to backup your files and reinstall your device! Don't forget to change passwords and notify your bank.
Prevention
- Don't root your Android device(s).
- Don't just install any app. Use common sense. When in doubt, do not install the app.
- Be wary of suspicious-looking apps even when they have a lot of positive feedback. These may be fake comments. Ask friends, colleagues or Google. Still not sure? Do not install the app.
- Download from official app stores only. Even though malware may exist on Google's Play store, chances are less likely.
- Use the default, built-in security in Android. For example, do not allow installation of apps from unknown sources and Encrypt Device.
- Always verify app permissions. Depending on the app, it should not be able to directly call other phone numbers.
- Back up your files. If something like this ever happens to you, simply reinstall and restore.
- Install an antivirus. This may be a resident one, meaning no active protection and scanning only.
More useful links are listed below in the Resources section.
Conclusion
While Windows malware still takes the biggest portion, malware for other operating systems is becoming more and more common. In regards to Android, make sure to follow the prevention tips above to stay safe.
Worth noting that, as always, prevention is better than disinfection. Create (and test) back-ups.
Resources
Analysing Android files - Blaze's Security Blog
Dealing with System Problems in Android: Safe Mode, Factory Reset & Restoring Backups - MakeUseOf
DevicePolicyManager - Android developer area
F-Secure Freedome VPN - F-Secure
How Do I Delete Applications from My Android Device? - Lifewire
The best antivirus software for Android - AV-Test
What Is A Nandroid Backup and How Exactly Does It Work? - MakeUseOf
IOCs






