Recently, an update of the infamous CryptoWall ransomware (or cryptoware) was released - you can read more about that particular ransomwere here:
CryptoWall 4.0 released with new Features such as Encrypted File NamesAdditionally, another ransomware variant has made a return, read more about that one here:
“Offline” Ransomware Encrypts Your Data without C&C CommunicationAnd let's not forget about this one either:
Chimera Ransomware focuses on business computersDid I mention yet there's ransomware for Linux as well? Have a look at
Linux.Encoder.1 while you're at it.
... But wait, there's more! You've guessed it, yet another ransomware variant has returned. I wonder what's going on these days, the (cyber)criminals seem to get even more competitive.
Lawrence Abrams over at
Bleeping Computer recently wrote an article about the variant we have here as well, as we have caught an updated variant of Poshcoder or Poshkoder or Power Worm:
Shoddy Programming causes new Ransomware to destroy your DataMoving on to the infection vector and process:
Kan du kontrollera den bifogade filen och låt mig veta vad du tycker? Tack
I just got this document, could you please check it and get back to me? Thanks
Email headers indicate:
Received: from techdallas.xyz (45.63.12.192.vultr.com [45.63.12.192])45.63.12.192 -
IPvoid -
WhoisAttached is a file called
Bilaga.doc or
Document.doc. Other variations are possible, depending on the language (in this case either Swedish or English).
Let's see what's inside Bilaga.doc:
 |
| Ole10Native is in fact a VBS file |
As you can see, there's an ObjectPool present, containing an Ole native file. The former contains storages for embedded OLE objects. In this case, it's containing a VBS file:
The VBscript uses Powershell with certain flags or parameters to download a file to the %TEMP% folder and execute it:
(Note that by default PowerShell is configured to prevent the execution of PowerShell scripts on Windows systems)
- -WindowStyle hidden: don't display anything to the user (set WindowStyle as hidden)
- -ExecutionPolicy Bypass: no scrips are blocked, neither are there any warnings or prompts
- -nologo: starts the PowerShell console without displaying the copyright banner
- -noprofile: tells PowerShell to not load profile (user) scripts
You can find a tad more information on these commands
here.
But what is the user seeing? Opening the Word document, there's another, clickable 'document':
 |
| Clicking the icon, warning message from Word |
 |
| Decoy message |
Then nothing happens, except in the background:
 |
| PowerShell download & running the malware |
Another PowerShell script (
.ps1 file) is being executed, which will start encrypting files with the following extensions:
"*.pdf","*.xls","*.docx","*.xlsx","*.mp3","*.waw","*.jpg","*.jpeg","*.txt","*.rtf","*.doc","*.rar","*.zip","*.psd","*.tif","*.wma","*.gif","*.bmp","*.ppt","*.pptx","*.docm","*.xlsm","*.pps","*.ppsx","*.ppd","*.eps","*.png","*.ace","*.djvu","*.tar","*.cdr","*.max","*.wmv","*.avi","*.wav","*.mp4","*.pdd","*.php","*.aac","*.ac3","*.amf","*.amr","*.dwg","*.dxf","*.accdb","*.mod","*.tax2013","*.tax2014","*.oga","*.ogg","*.pbf","*.ra","*.raw","*.saf","*.val","*.wave","*.wow","*.wpk","*.3g2","*.3gp","*.3gp2","*.3mm","*.amx","*.avs","*.bik","*.dir","*.divx","*.dvx","*.evo","*.flv","*.qtq","*.tch","*.rts","*.rum","*.rv","*.scn","*.srt","*.stx","*.svi","*.swf","*.trp","*.vdo","*.wm","*.wmd","*.wmmp","*.wmx","*.wvx","*.xvid","*.3d","*.3d4","*.3df8","*.pbs","*.adi","*.ais","*.amu","*.arr","*.bmc","*.bmf","*.cag","*.cam","*.dng","*.ink","*.jif","*.jiff","*.jpc","*.jpf","*.jpw","*.mag","*.mic","*.mip","*.msp","*.nav","*.ncd","*.odc","*.odi","*.opf","*.qif","*.xwd","*.abw","*.act","*.adt","*.aim","*.ans","*.asc","*.ase","*.bdp","*.bdr","*.bib","*.boc","*.crd","*.diz","*.dot","*.dotm","*.dotx","*.dvi","*.dxe","*.mlx","*.err","*.euc","*.faq","*.fdr","*.fds","*.gthr","*.idx","*.kwd","*.lp2","*.ltr","*.man","*.mbox","*.msg","*.nfo","*.now","*.odm","*.oft","*.pwi","*.rng","*.rtx","*.run","*.ssa","*.text","*.unx","*.wbk","*.wsh","*.7z","*.arc","*.ari","*.arj","*.car","*.cbr","*.cbz","*.gz","*.gzig","*.jgz","*.pak","*.pcv","*.puz","*.r00","*.r01","*.r02","*.r03","*.rev","*.sdn","*.sen","*.sfs","*.sfx","*.sh","*.shar","*.shr","*.sqx","*.tbz2","*.tg","*.tlz","*.vsi","*.wad","*.war","*.xpi","*.z02","*.z04","*.zap","*.zipx","*.zoo","*.ipa","*.isu","*.jar","*.js","*.udf","*.adr","*.ap","*.aro","*.asa","*.ascx","*.ashx","*.asmx","*.asp","*.indd","*.asr","*.qbb","*.bml","*.cer","*.cms","*.crt","*.dap","*.htm","*.moz","*.svr","*.url","*.wdgt","*.abk","*.bic","*.big","*.blp","*.bsp","*.cgf","*.chk","*.col","*.cty","*.dem","*.elf","*.ff","*.gam","*.grf","*.h3m","*.h4r","*.iwd","*.ldb","*.lgp","*.lvl","*.map","*.md3","*.mdl","*.mm6","*.mm7","*.mm8","*.nds","*.pbp","*.ppf","*.pwf","*.pxp","*.sad","*.sav","*.scm","*.scx","*.sdt","*.spr","*.sud","*.uax","*.umx","*.unr","*.uop","*.usa","*.usx","*.ut2","*.ut3","*.utc","*.utx","*.uvx","*.uxx","*.vmf","*.vtf","*.w3g","*.w3x","*.wtd","*.wtf","*.ccd","*.cd","*.cso","*.disk","*.dmg","*.dvd","*.fcd","*.flp","*.img","*.iso","*.isz","*.md0","*.md1","*.md2","*.mdf","*.mds","*.nrg","*.nri","*.vcd","*.vhd","*.snp","*.bkf","*.ade","*.adpb","*.dic","*.cch","*.ctt","*.dal","*.ddc","*.ddcx","*.dex","*.dif","*.dii","*.itdb","*.itl","*.kmz","*.lcd","*.lcf","*.mbx","*.mdn","*.odf","*.odp","*.ods","*.pab","*.pkb","*.pkh","*.pot","*.potx","*.pptm","*.psa","*.qdf","*.qel","*.rgn","*.rrt","*.rsw","*.rte","*.sdb","*.sdc","*.sds","*.sql","*.stt","*.t01","*.t03","*.t05","*.tcx","*.thmx","*.txd","*.txf","*.upoi","*.vmt","*.wks","*.wmdb","*.xl","*.xlc","*.xlr","*.xlsb","*.xltx","*.ltm","*.xlwx","*.mcd","*.cap","*.cc","*.cod","*.cp","*.cpp","*.cs","*.csi","*.dcp","*.dcu","*.dev","*.dob","*.dox","*.dpk","*.dpl","*.dpr","*.dsk","*.dsp","*.eql","*.ex","*.f90","*.fla","*.for","*.fpp","*.jav","*.java","*.lbi","*.owl","*.pl","*.plc","*.pli","*.pm","*.res","*.rsrc","*.so","*.swd","*.tpu","*.tpx","*.tu","*.tur","*.vc","*.yab","*.8ba","*.8bc","*.8be","*.8bf","*.8bi8","*.bi8","*.8bl","*.8bs","*.8bx","*.8by","*.8li","*.aip","*.amxx","*.ape","*.api","*.mxp","*.oxt","*.qpx","*.qtr","*.xla","*.xlam","*.xll","*.xlv","*.xpt","*.cfg","*.cwf","*.dbb","*.slt","*.bp2","*.bp3","*.bpl","*.clr","*.dbx","*.jc","*.potm","*.ppsm","*.prc","*.prt","*.shw","*.std","*.ver","*.wpl","*.xlm","*.yps","*.md3","*.1cd"
As you can see, it has covered quite a lot of extensions.
Nathan Scott from Bleeping Computer provided an image with a great explanation on what the script does:
In the version I saw, the PowerShell scripts were slightly different, in fact an 'improved version'.
After encrypting all your files, it will drop an HTML file (named
DECRYPT_INSTRUCTION.html) on the root of all your folders which contains the following message:
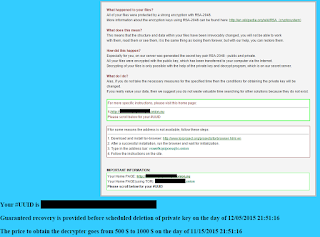 |
| Ransom message - you may need to pay up to $ 1000 |
It generates your #UUID by the following simple PowerShell command:
Get-wmiobject Win32_ComputerSystemProduct UUID
When visiting said Onion (Tor) link:
 |
| Unlock message |
Difference here from the version of October is that they also offer to decrypt 1 file, as proof they can actually decrypt all your files again. Unfortunately, the encryption fails horribly (for example, no extension is appended) and your files will be unrecoverable. For more information, see
here.
Prevention- Don't open attachments from unknown senders - ever.
- Install an antivirus and keep it up-to-date and running. Enable the option to scan Compressed Files.
- Consider disabling Windows Script Host. You can use my tool, Rem-VBSworm with option D for example.
- Alternatively, you can install Analog X's Script Defender, which will block these scripts (JS, VBS, ...) as well.
- Consider disabling PowerShell if you don't need or use it. There are two possible options:
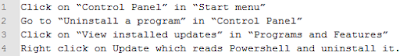

Note that if you have a company laptop, you should inform with your network administrator first. - Improve security for your Microsoft Office package. (Word, Excel, ...)
This means disabling ActiveX, disabling macros and blocking external content. Useful links:
Enable or disable ActiveX controls in Office documents
Enable or disable macros in Office documents
Block or unblock external content in Office documents - As with all ransomware cases: take backups!
Some time ago, I did a Q&A on ransomware, which also included several general tips on how to prevent (ransomware and other) malware. You can find and read those tips
here.
Disinfection - Identify and kill malicious processes (use Task Manager for example). In this specific case:
winword.exe, wscript.exe, powershell.exe - Run a full scan with your installed antivirus product.
- Run a full scan with another antivirus and/or antimalware product.
- In a company: unplug your network cable & warn your network administrator immediately!
Conclusion
Ransomware is far from dead (that is, encrypting ransomware or cryptoware, the "old" ransomware isn't very much around anymore), thus it's important to take preventive measures as outlined above.
Resources
Acknowledgments
Thanks to my colleague Ville from Panda Security Sweden for alerting me about this incident and Lawrence & Nathan over at Bleeping Computer for their already available information.
 Personally I'm not convinced that having numbers in Blogger URL's is a problem.
Personally I'm not convinced that having numbers in Blogger URL's is a problem.































