Unless you haven't accessed the internet for a week, you must have heard about WannaCry or one of the aliases it uses, such as WannaCryptor, WanaCry or WanaDecrypt0r.
In this blog post, I'll try to answer, in clear & concise language, some of the most asked questions. While there have been several excellent (technical) blog posts about WannaCry, this one will be purely non-technical and focuses on practical steps.
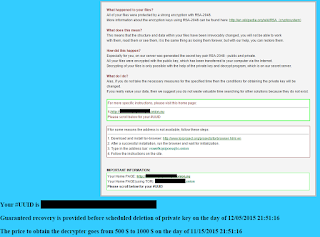
What is WannaCry?
The most obvious question, but not necessarily an obvious answer. In essence, it is ransomware, software that holds your machine and your files ransom, until a fee is paid.
In its latest version, it also introduced a wormable component; in other words, it could spread to other machines running Windows in your network.
A worm is a type of malware that can replicate itself and thus spread to other machines in a network.
The name 'WannaCry' stems from the ransomware authors themselves, as that is how they named it.
How does WannaCry work?
An excellent infographic explaining how WannaCry works already exists - see below:
 |
| Figure 1 - How does the WannaCry ransomware work? (Source) |
Which operating systems does WannaCry infect?
Windows only. More specifically: Windows XP up to Windows 10, Windows Server 2003 up to Windows server 2016. This is the ransomware in its pure form only, however. (see questions below)
Which operating systems were affected the most?
Most of the operating systems or machines were running Windows 7.
 |
| Figure 2 - affected Windows versions by % (Source) |
Can I spread WannaCry unwillingly to others, or in my network?
It is definitely possible, but only if the worm component is active and you have not updated Windows in a while. More specifically, you will need to install MS17-010 to 'close the hole' or patch the vulnerability.
When did the outbreak of WannaCry start?
The outbreak reportedly started last week Friday, 12/05/2017, in the morning hours (UTC). However; it is possible the outbreak started the evening before that. A sudden spike in internet traffic seems to suggest the worm started spreading that night:
 |
| Figure 3 - possible related spike in traffic (Source) |
Can something like this happen again?
Defnitely. In fact, some malware families also exploit(ed) the same vulnerability in Windows as mentioned above.
What is or was the WannaCry 'kill switch'?:
The Wikipedia definition of a kill switch is as follows:
A kill switch is a security measure used to shut off a device in an emergency. (Source)This is no different in WannaCry: a specific domain was embedded in the ransomware to act as a kill switch: if said domain exists & communicates this to the ransomware; exit immediately.
Thanks to MalwareTech, who registered the domain, a lot of the WannaCry infections were unable to spread further, since the domain now existed.
Note that some variants appeared later with other 'kill switch domains', which were also rather quickly registered by other security researchers.
Can I decrypt or recover files encrypted by WannaCry?
It is possible. A tool, WannaKiwi, has been developed by several security researchers which may be able to restore your files.
Please find below:
- Download the tool - https://github.com/gentilkiwi/wanakiwi/releases
- Information about the tool - https://github.com/gentilkiwi/wanakiwi
- More info and background - https://blog.comae.io/wannacry-decrypting-files-with-wanakiwi-demo-86bafb81112d
The tool will work granted you have not killed the ransomware process (or your antivirus didn't), and/or you didn't reboot your machine.
What if the tool doesn't work? Can I restore my files in any other way?
If the tool doesn't work, you may have rebooted your machine, the ransomware may have been removed or its process killed.
If you are still desperate to get your files back, there's always a possibility using...:
- ... Backups! If you have backups, please do try restoring from a backup first.
- ... Shadow Copies (Restore Previous Versions). If this doesn't work, you can use ShadowExplorer for example.
- ... Using data recovery software like Recuva, or for a bigger chance in restoring your files, PhotoRec.
Will I get my files back if I pay the ransomware?
There is no sure way of telling. The general advise is, as always, to NOT pay. A few reasons why not:
- The decrypter they send may not work at all, or does nothing.
- They don't send any decrypter at all.
- They cannot contact you or you cannot contact them for whichever reason.
- You are contributing to the 'ransomware eco-system', thus ensuring and increasing the amount of (new) ransomware that will emerge.
And:
- You are dealing with criminals in the end. Cybercriminals, but criminals. This means there is no way of telling if they will hold up their end of the bargain.
If you can avoid it, DO NOT PAY!
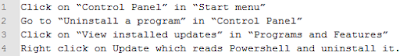
How do I remove the ransomware itself?
Any antivirus and/or antimalware by now detects all versions of WannaCry.
How can I defend myself or the other machines in my network against this attack?
Specifically against the worm component, you will need to install patch MS17-010 as mentioned above. If you are using an older version of Windows, for example Windows XP, please see below:
https://blogs.technet.microsoft.com/msrc/2017/05/12/customer-guidance-for-wannacrypt-attacks/
The link here above is worth a read regardless if you have Windows XP, or a newer operating system version of Windows. If you are still using Windows XP, please do consider to upgrade to a newer version of Windows. Some computer stores may be able to offer you a discount.
Note that by default, Windows updates will be performed automatically.
You may want to check if automatic updates are enabled, by reading the following article:
How to configure and use Automatic Updates in Windows
Additionally, you will need an antivirus and a firewall. If you use Windows 7 or above, the Windows firewall is fairly decent. A free antivirus will, in most cases, suffice as well.
However, it may be worthwhile considering a full antivirus package, which usually includes better antivirus protection and a better firewall. (and additional features, such as anti-spam for example)
How can I protect my files from being encrypted or targeted by ransomware such as WannaCry?
The best recommendation of all times, is to create backups.
Many free backup solutions exist to create copies of your files (pictures, documents, ...). An overview of no less 34 backup solutions can be found here:
34 Free Backup Software Tools
You may also want to give the following article a read:
7 Backup Strategies for Your Data, Multimedia, and System Files
It may seem a lot of work initially, but it is definitely worth it.
A few points to consider when making backups:
Can I report someone, somewhere, somehow about this ransomware if it affected me?
Surely. You can fill out an online form via the following portals:
It is very important you report the incident. The more information that is available to law enforcement, the bigger the chance they can catch and arrest the people behind WannaCry, or others.
Unfortunately, should you have paid, but your files are still encrypted, there is no sure way of telling if you'll be able to recover any monetary losses. Therefore, the advise is to NOT pay the ransom.
That's it, I hope you have been better informed! Unless of course...
I would like to read more. Where can I find more information?
I have setup a whole page on ransomware prevention, which you can flick through.
Any other questions, please do not hesitate to post in the comments, or send me a message on Twitter.
Specifically against the worm component, you will need to install patch MS17-010 as mentioned above. If you are using an older version of Windows, for example Windows XP, please see below:
https://blogs.technet.microsoft.com/msrc/2017/05/12/customer-guidance-for-wannacrypt-attacks/
The link here above is worth a read regardless if you have Windows XP, or a newer operating system version of Windows. If you are still using Windows XP, please do consider to upgrade to a newer version of Windows. Some computer stores may be able to offer you a discount.
Note that by default, Windows updates will be performed automatically.
You may want to check if automatic updates are enabled, by reading the following article:
How to configure and use Automatic Updates in Windows
Additionally, you will need an antivirus and a firewall. If you use Windows 7 or above, the Windows firewall is fairly decent. A free antivirus will, in most cases, suffice as well.
However, it may be worthwhile considering a full antivirus package, which usually includes better antivirus protection and a better firewall. (and additional features, such as anti-spam for example)
How can I protect my files from being encrypted or targeted by ransomware such as WannaCry?
The best recommendation of all times, is to create backups.
Many free backup solutions exist to create copies of your files (pictures, documents, ...). An overview of no less 34 backup solutions can be found here:
34 Free Backup Software Tools
You may also want to give the following article a read:
7 Backup Strategies for Your Data, Multimedia, and System Files
It may seem a lot of work initially, but it is definitely worth it.
A few points to consider when making backups:
- Don't leave your external drive plugged in after the backup. This to prevent your backup files will be encrypted as well. So, take your backup and disconnect your external hard drive afterwards.
- Be careful with backups in the cloud as well. If you use Dropbox for example, and it syncs to your Dropbox folder after your data has been encrypted... You will have another copy of your encrypted data.
- Test your backup, if possible. You wouldn't want to encounter an infection then to only find out your backups are corrupted somehow.
- You can also write your backups to write-once media, like for example DVDs or Blue-Ray. Easier is of course using an external hard drive, but don't forget to disconnect it after you have made the backup.
Can I report someone, somewhere, somehow about this ransomware if it affected me?
Surely. You can fill out an online form via the following portals:
- Report Cybercrime Online (European Union, United Kingdom)
- Internet Crime Complaint Center (United States)
Alternatively, you may want to use my online form to fill in, (print out,) and hand over a copy to your local police department, or Computer Emergency Response Team.
Find the form here; Cybercrime Report Template
It is very important you report the incident. The more information that is available to law enforcement, the bigger the chance they can catch and arrest the people behind WannaCry, or others.
Unfortunately, should you have paid, but your files are still encrypted, there is no sure way of telling if you'll be able to recover any monetary losses. Therefore, the advise is to NOT pay the ransom.
That's it, I hope you have been better informed! Unless of course...
I would like to read more. Where can I find more information?
I have setup a whole page on ransomware prevention, which you can flick through.
Any other questions, please do not hesitate to post in the comments, or send me a message on Twitter.