Unless you didn't have any internet access today, you must have heard about the compromise of PHP.net today. An excerpt:
| One of the first confirmations that PHP.net |
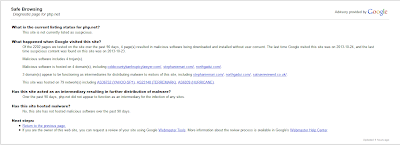 |
| Google Safe Browsing warning |
You can read the full discussion on whether PHP was compromised or not here:
Statements by PHP.net itself:
I think it's pretty clear by now how it (could have) happened: insertion of a malicious - or change of- a Javascript file on their website.
Let's start with the first entry of infection, most likely userprefs.js on the main page. Some heavily obfuscated Javascript is present, which redirects to either:
| Redirects |
Here's a Pastebin link containing the modified userprefs.js: http://pastebin.com/yZWxxk2h
After either of those redirects, PluginDetect (which is a legit Javascript library to detect browser plugins) determines your version of Adobe & Java. If you have any of those vulnerable versions installed, you'll get served with several flavors of malware. Your browser will either crash or "hang" for a while.
Interestingly enough, another PluginDetect was also trying to check for vulnerable versions of VLC, SilverLight and Flash.
If you don't have any of these installed, you're possibly being redirected to a website with the text "He took over Russia with a wooden plough, but left it equipped with atomic weapons" (seems to be a letter about Stalin, see here) which contains the following fancy YouTube video:
http://www.youtube.com/watch?v=9Mnmhtr4ThE
http://www.youtube.com/watch?v=9Mnmhtr4ThE
Let's move on to the actual payload. Thanks to a blogpost by Barracuda Labs, I was able to download the PCAP file they gathered.
The PCAP file proved to be very interesting. Besides being able to pull the usual malicious Javascript files, I was able to gather some payloads as well, which aren't very friendly to your machine.
The following malware was seen to be downloaded: Fareit, ZeroAccess (GoogleUpdate/Google Desktop variant), Zeus and even ransomware (unknown) in one instance!
Fareit and Zeus/Zbot have been known for going hand in hand for some time now, see here for an earlier blogpost. When executed, you'll either have to pay up a fine (ransomware), get a rootkit (ZeroAccess) or get your information stolen (Fareit & Zeus). An overview of the information that will be stolen:
 |
| Your data being stolen |
I don't need to mention that this is quite bad. Have you visited PHP.net yesterday or today and saw your browser crash? Did you notice any strange behavior? Yes? No? Either way, perform a scan of your machine right away. We'll get back to that though.
MD5s of samples gathered:
c73134f67fd261dedbc1b685b49d1fa4406d6001e16e76622d85a92ae3453588
dc0dbf82e756fe110c5fbdd771fe67f5
78a5f0bc44fa387310d6571ed752e217
18f4d13f7670866f96822e4683137dd6
Callbacks:
85.114.128.127
Prevention
- Patch your Java & Adobe or uninstall it if you don't need it.
Same goes for their browser plugins or add-ons! - Keep your browser of choice up-to-date.
- Install an antivirus and antimalware product and keep it up-to-date & running.
- Use NoScript in Firefox or NotScripts in Chrome.
- Block the above IP. (either in your firewall or host file)
Disinfection
- Perform a full scan with your installed antivirus and a scan with another antivirus or antimalware product. You can check on VirusTotal which antivirus applications already detect this malware.
Conclusion
- Every website can be injected with malicious Javascript, even well-known websites!
- Received a Google Safe Browsing warning? Don't simply ignore it, either look up if anything's known about that website being hacked or if you're not sure, stay away from it for a while. (best case is to contact the site owner as well.)


