Tuesday, 10 May 2011
Tuesday, 26 April 2011
Technoviking ? I am not amused
So yesterday I was looking on Google Images for the 'Technoviking'. I'm sure most of you know the guy/meme but just to be sure:

http://knowyourmeme.com/memes/technoviking
In case you're wondering, I do not remember why he flashed in my mind all of a sudden, but I was listening to some music on Youtube and I suppose there was a Suggested Video .
.
Either way, some of the Google Images were in fact redirecting to a scareware page, urging you to download a file to "clean" your computer. Some of the images that were infected:

Some infected Google Image results
If you click on any of them, you would get the following message:

"Windows Security" will perform a fast scan of system files
... and when clicking on "OK" you'll get the well-known fake scanning page:

Fake Scanning page finding numerous infections
The following file was downloaded:
BestAntivirus2011.exe
Result: 18/41 (43.9%)
MD5: e705b657f5830eb2a43eee3a32f549c3
VirusTotal Report
ThreatExpert Report
Anubis Report
Today I checked again and the scareware/rogueware campaign is still active. I was now presented with another file that has a very low detection rate on VirusTotal:
BestAntivirus2011.exe
Result: 2/41 (4.9%)
MD5: 56ce5479183913f2082bf0fd790dbaea
VirusTotal Report
The payload is a rogueware called 'MS Removal Tool'.
When executing the dropped file (BestAntivirus2011.exe) :

MS Removal Tool fake scanning screen
It is interesting to note that you would only get redirected when using Internet Explorer or Google Chrome. Neither on Firefox 3.6 or Firefox 4.0 the redirect would commence.
Prevention
- Be careful when visiting any webpage. A useful trick is to check the real URL behind the image. Most of the times you can verify this by checking in the left corner of your browser:

Clicked on a picture and started loading this website instead of the original one
- Use browser extentions to verify the integrity of an image or URL. Useful add-ons for Google Chrome are for example VTchromizer, NotScripts and WOT .
- Keep your Antivirus and browser, as well as your browser add-ons up-to-date.
- If it is too late and a 'scan' is already starting, immediately close your browser by bringing up Task Manager (CTRL + ALT + DEL) and killing your browser's process:
Desinfection
If the harm is already done and you are getting warnings, messages or pop-ups stating you are infected and you need to take 'immediate action' to clean your computer, follow the guide below at BleepingComputer's to rid yourself of this malware:
Remove MS Removal Tool
Conclusion
Don't be fooled by Google's preview of images, you can still get infected even though the site appears to be safe.
Follow the above prevention tips to decrease the chance of your computer becoming infected.

http://knowyourmeme.com/memes/technoviking
In case you're wondering, I do not remember why he flashed in my mind all of a sudden, but I was listening to some music on Youtube and I suppose there was a Suggested Video
Either way, some of the Google Images were in fact redirecting to a scareware page, urging you to download a file to "clean" your computer. Some of the images that were infected:

Some infected Google Image results
If you click on any of them, you would get the following message:

"Windows Security" will perform a fast scan of system files
... and when clicking on "OK" you'll get the well-known fake scanning page:

Fake Scanning page finding numerous infections
The following file was downloaded:
BestAntivirus2011.exe
Result: 18/41 (43.9%)
MD5: e705b657f5830eb2a43eee3a32f549c3
VirusTotal Report
ThreatExpert Report
Anubis Report
Today I checked again and the scareware/rogueware campaign is still active. I was now presented with another file that has a very low detection rate on VirusTotal:
BestAntivirus2011.exe
Result: 2/41 (4.9%)
MD5: 56ce5479183913f2082bf0fd790dbaea
VirusTotal Report
The payload is a rogueware called 'MS Removal Tool'.
When executing the dropped file (BestAntivirus2011.exe) :

MS Removal Tool fake scanning screen
It is interesting to note that you would only get redirected when using Internet Explorer or Google Chrome. Neither on Firefox 3.6 or Firefox 4.0 the redirect would commence.
Prevention
- Be careful when visiting any webpage. A useful trick is to check the real URL behind the image. Most of the times you can verify this by checking in the left corner of your browser:

Clicked on a picture and started loading this website instead of the original one
- Use browser extentions to verify the integrity of an image or URL. Useful add-ons for Google Chrome are for example VTchromizer, NotScripts and WOT .
- Keep your Antivirus and browser, as well as your browser add-ons up-to-date.
- If it is too late and a 'scan' is already starting, immediately close your browser by bringing up Task Manager (CTRL + ALT + DEL) and killing your browser's process:
- a) For Google Chrome: chrome.exe or chrome.exe *32
- b) For Mozilla Firefox: firefox.exe or firefox.exe *32
- c) For Microsoft's Internet Explorer: iexplore or iexplore.exe *32
Desinfection
If the harm is already done and you are getting warnings, messages or pop-ups stating you are infected and you need to take 'immediate action' to clean your computer, follow the guide below at BleepingComputer's to rid yourself of this malware:
Remove MS Removal Tool
Conclusion
Don't be fooled by Google's preview of images, you can still get infected even though the site appears to be safe.
Follow the above prevention tips to decrease the chance of your computer becoming infected.
Labels:forex, iqoption, pubg Hacked
fakeAV,
google image poisoning,
google images,
low detection,
malware,
rogueware,
scareware,
technoviking
Wednesday, 13 April 2011
Facebook Support. Personal data has been changed!
There appears to be a new malicious email being sent out with the subject: "Facebook Support. Personal data has been changed! ID75300"
In a previous post I already explained a similar campaign:
Your FaceBook password has been changed
In a previous post I already explained a similar campaign:
Your FaceBook password has been changed
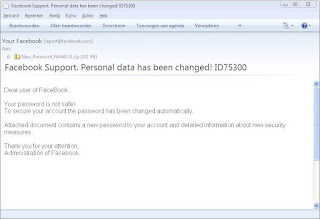
First of all, you would receive an email similar to this one:
Email claiming your personal data has been changed.
The email content is the following:
Dear user of FaceBook.
Your password is not safe! To secure your account the password has been changed automatically.
Attached document contains a new password to your account and detailed information about new security measures.
Thank you for your attention,
Administration of Facebook.
Your password from Facebook appears to be unsafe and you need to verify attached document to view your new login information. There is a file attached called "New_Password_NU44133.zip"
Inside the ZIP file you will find a file called New_Password.exe:
The file New_Password.exe is in fact not a Microsoft Word document, as you may suspect from the icon, but is in fact a malicious executable:
New_Password.exe
Result: 19/42 (45.2%)
MD5: 99a7cc6e674b94fbecef52f520c03dc3
The file also drops the following executable on the system:
aspimgr.exe
Result: 39/42 (92.9%)
MD5: 4531d9d75dab83c957122538b6fc92ba
The executable also tries to connect (called "phoning home") to download additional malware. However, at time of writing the URLs were offline.
Conclusion
If you receive emails like this, you should already be alerted:
"Why would Facebook send me an email my password has been changed ?"
The answer is simple: they don't. Whether you have Facebook or not, instantly delete the email and don't look back.
Increase in Dutch banking phishing
Recently I made a post on Malware Disasters about an increase of targeted phishing in the last few monts. The focus was mainly on Dutch (and Belgian) customers of respectively Rabobank and ING, two major banks.
Here's a small excerpt:
You can read the full article here:
http://malwaredisasters.blogspot.com/2011/04/increase-in-dutch-banking-phishing.html
You can also download a Dutch (Nederlands) translation from the following link:
Click HERE to download. (hosted on Uploading.com)
Conclusion
The following tips do not only apply to the above story, but apply to any other (suspicious) email you receive:
Here's a small excerpt:
The last few months there was an increase in a phishing campaign targeted on customers from Rabobank and ING, two major banks in The Netherlands and Belgium. Some examples of a phishing mail:
Phishing email for ING with the subject “Account Verificatie” (or in English: “Account Verification”)
You can read the full article here:
http://malwaredisasters.blogspot.com/2011/04/increase-in-dutch-banking-phishing.html
You can also download a Dutch (Nederlands) translation from the following link:
Click HERE to download. (hosted on Uploading.com)
Conclusion
The following tips do not only apply to the above story, but apply to any other (suspicious) email you receive:
- Do not click on any of the links (or anything for that matter) in the email you have received.
- Do not reply to the email.
- Delete the email immediately, certainly if you are not a customer of the aforementioned bank or did not order anything, changed your password, and so on.
- If you really need to access or check your bank account, visit the website directly by typing the address in your browser’s address bar. Also verify the URL starts with https instead of http.
- Another useful trick is to hover over the link in the email. In the bottom left corner you should be able to see the real address behind the URL displayed.
- When in doubt, you can double-check using URL scanning services such as VirusTotal or URLVoid
Labels:forex, iqoption, pubg Hacked
blog update,
ING,
phishing,
rabobank,
Spam,
spear phishing
Wednesday, 16 March 2011
FedEx notification #85645
You might have read my previous blog post:
This time it's FedEx to be the subject of a new and highly active spam campaign.
I received different emails, all containing a notification I can find more information about my package in attachment. The subject of one of these mails was "FedEx notification #85645"
They all have a different tracking number behind the #, but the content is always the exact same thing:
Dear customer.
The parcel was sent your home address.
And it will arrive within 7 business day.
More information and the tracking number are attached in document below.
Thank you. © FedEx 1995-2011
In all of these spam emails, you will find an attachment, which can be called either
FedEx letter.zip, FedEx notice.zip or document.zip.
Document.exe attached to email
Just like the case for the UPS spam campaign, again an Adobe Acrobat icon to trick you. In fact this "Document" file is not a PDF file, but an executable which can infect your computer.
Document.exe
Result: 15/43 (34.9%)
MD5: 09410950dd80df3083ae87cf839643e2
FedEx notice.exe
So far the subject of this FedEx may differ from these 3:
FedEx notification #[random number]
FedEx Reminder – Invoice [random number]
FedEx ticket #[random number]
Conclusion
You should never trust an email which has:
- only a URL included in the message
- an attachment that you need to open to view 'information'
- crappy spelling and grammar if there is content in the message
- been sent out to everyone in the sender's address book
- been sent from an unknown sender
- promises you can buy something for a very cheap price
- No subject or strange subjects ( eg.: "0 enjoy yourself" )
Never reply to this kind of email, but delete it immediately without opening it.
If you have (unintentionally) downloaded a program and you are unsure about its intentions, you can always upload it to VirusTotal or other online virus scanners (VirScan, Jotti). Keep in mind that if a file is not detected by any engine, it is not necessarily clean!
Labels:forex, iqoption, pubg Hacked
blog update,
FedEx,
malware,
PDF,
Spam
Subscribe to:
Comments (Atom)