Today I was brought to the attention of a Tumblr post - apparently there's malware doing the rounds making use of Steam chat, (adding Steam friends and) spamming Steam users.
Example message:
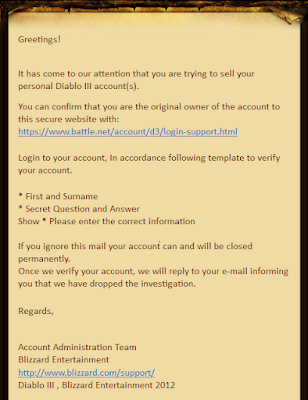
 |
| "karpathos" sending a bit.ly link (Image source) |
Onyx is right, the link's indeed phishy and uses bit.ly (a URL shortener) to trick users into clicking it. Remember the worm that spread via Skype and Messenger last year? (reference here and here) This is a similar campaign.
Setup
Someone adds you on Steam, you accept and immediately a chat pops up as similar to above.
Alternatively someone from your friends list already got infected and is now sending the same message to all his/her friends.
The bit.ly link actually refers to a page on Google Drive, which immediately downloads a file called IMG_211102014_17274511.scr, which is in fact a Screensaver file - an executable.
The file is shared by someone named "qwrth gqhe". Looks legit.
Note that normally, the Google Drive Viewer application will be shown and this will allow you to download the .scr file. In this case, the string "&confirm=no_antivirus" is added to the link, which means the file will pop-up immediately asking what to do: Run or Save.
(and in some cases download automatically)
At time of writing, the file is actually still being hosted by Google Drive. I have reported it however.
Afterwards, you're presented with the screensaver file which has the following icon:
 |
| Image of IMG_211102014_17274511.scr file |
Opening the file will result in installing malware on your system, which will steal your Steam credentials.
Technical details
IMG_211102014_17274511.scr
Original Filename: wrrrrrrrrrrrr.exe
Type: PE32 executable for MS Windows (GUI) Intel 80386 32-bit Mono/.Net assembly
SHA1: 7d0575a883fed7a460b49821c7d81897ae515d43
VirusTotal: link
185.36.100.181
 |
| Server in Czech Republic. VirusTotal reference |
Downloads and executes:
temp.exe
Type: PE32 executable for MS Windows (GUI) Intel 80386 32-bit Mono/.Net assembly
SHA1: cd9b3bf5c8d70e833b5c580c9b2fc1f3e5e4341e
VirusTotal: link
 |
| Interesting information in the debug path, note the "steamstealer" string. |
Remediation
What if you clicked the link and executed the file? Follow these steps:
- Exit Steam immediately
- Open up Task Manager (CTRL + SHIFT + ESC) and find a process called temp.exe, wrrrrrrrrrrrr.exe, vv.exe or a process with a random name, for example 340943.exe or a process similar to the file you executed
- Launch a scan with your installed antivirus
- Launch a scan with another, online antivirus or install & scan with Malwarebytes
- When the malware has been disinfected or deleted, change your Steam password - if you use the same password for other sites, change those as well
- De-authorize any unknown machines, read how to do that here:
Family Library Sharing User Guide - Verify none of your Steam items are missing - if so, it is advised to reinstall Steam as well.
Note: move the Steamapps folder (default on C:\Program Files\Steam\Steamapps) outside of the Steam directory to prevent your games from being deleted - Contact Steam/Valve in order to get your items back:
Send a ticket to Steam support
Prevention
- Be wary when someone new or with Level 0 adds you on Steam and immediately starts sending links
- In fact, don't click on links someone unknown sends to you
- If you receive a link which is a URL shortener (bit.ly or goo.gl for example), you can use GetLinkInfo to see the real URL
- If you did click the link, don't open or execute anything else - just close the webpage (if any) or cancel the download
- By default, file extensions are not shown. Enable 'Show file extensions' to see the real file type. Read how to do that here
- Install WOT - WOT is a community-based tool and is therefore very useful for those fake screenshot websites, whereas other users can warn you about the validity.
- Follow the tips by Steam itself to further protect your account:
Account Security Recommendations - If you trade a lot or want to check if a Steam account has a bad reputation, you can use SteamRep:
https://steamrep.com/ - SteamRep has also set up a Safe Trading Practices guide.
- Consider setting up the Steam Guard Mobile Authenticator (2FA).
- There's a useful guide in preventing scams on this Reddit link as well.
- For sysadmins/network administrators, I have created an IOC on AlienVault OTX with all known (to me at least) SteamStealer IPs.
Conclusion
Never click on unknown links, especially when a URL shortener service like bit.ly is used. (others are for example t.co, goog.gl, tinyurl, etc.)
Don't be fooled by known icons or "legit" file descriptions, this can easily be altered.
Even if you clicked the link and you're not suspicious, you should be when a file is downloaded and it's (in this case) a screensaver file.
For checking what is really behind a short URL, you can use:
For checking whether a file is malicious or not:
Follow the prevention tips above to stay safe and protect yourself from the SteamStealer malware.